Be yourself; Everyone else is already taken.
— Oscar Wilde.
This is the first post on my new blog. I’m just getting this new blog going, so stay tuned for more. Subscribe below to get notified when I post new updates.
Be yourself; Everyone else is already taken.
— Oscar Wilde.
This is the first post on my new blog. I’m just getting this new blog going, so stay tuned for more. Subscribe below to get notified when I post new updates.
Cyber Bullying – Cyber bullying is world-wide, some people may not know they are being a cyber bully, for instance commenting negatively on someone’s picture thinking your having an opinion is cyber bullying. Lots of teenagers are cyber bullied online from their classmates which causes anxiety and often leading to self-harm and suicide.
Child Pornography – Unfortunately this is a crime which rakes in millions each year. Often sold on the dark web people will take photos, post photos and buy photos of children for their personal pleasure.
Hackers – The world is getting more and more scary online with all the cyber crimes, hacking if unethical is illegal and hackers will steal your data for their own potential gain or hate crime.
Trolling – A bit like cyber bullying, you are trolling people online commenting on their pictures having an opinion on the way a person behaves or acts. Usually not directed at the person but on social media forum.
Identity theft – Hackers using social media skills to gain access to personal information. This information can then be used to commit fraud and identity theft, i.e. get credit card/loan with someone else’s details.
Child sex abuse – Again usually on the dark web and illegal. Children from foreign countries as well as the EU are often pimped from a young age to travellers and videos are made and sold online of sexual acts. It is reported that young babies are often sexually abused and content streamed and sold to paedophiles online.
Black market Trading – Guns, exotic animal, drugs are a few of the illegal purchases that are made online, There is a marketplace on the dark web that you can buy almost anything imaginable.

PAS 555 -Supplies a holistic framework for effective cyber security which not only considers the technical aspects, but also the related physical, cultural and behavioural aspects of an organisation’s approach to addressing cyber threats, including effective leadership and governance. ref https://www.itgovernance.co.uk/shop/product/pas-555-2013-standard
ISO/IEC 27001:2013



CSA CCM – CSA(Cloud Security Alliance)’s CCM (Cloud Controls Matrix) is a set of controls designed to maximise information security for users of Cloud technologies.
Acceptable Use Policy (AUP) “An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to a corporate network or the Internet. Many businesses and educational facilities require that employees or students sign an acceptable use policy before being granted a network ID.” ref https://www.google.co.uk/search?
Access Control Policy (ACP) How organisations monitor which employees and departments have access to certain data. For example the technical team will need access to certain programmes but do not need access to HR documents and vice verse. The Access control policy makes sure everyone has access only what they need access too. If new access is required then a spark request is sent to ask permission and justify the reason for use.
Change Management Policy. It establishes the requirements for change to be managed and auditable, and to ensure business continuity.
Information Security Policy
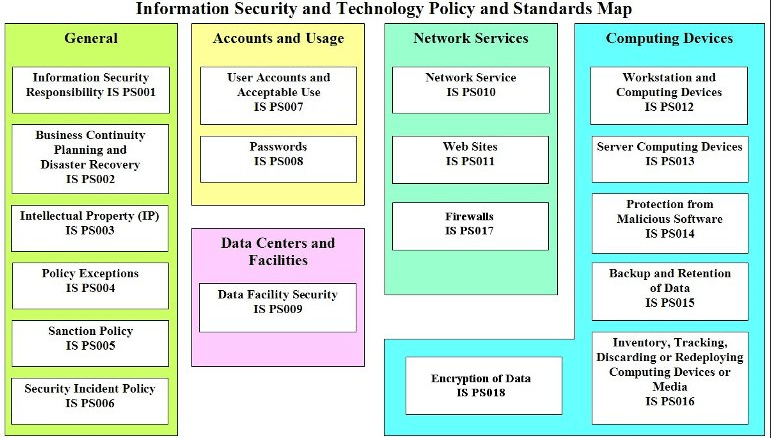
Protecting an organisation by ensuring all employees who use information technology assets within the organization, or its networks, comply with its stated rules and guidelines.
Incident Response (IR) Policy – This can be any incident in an organisation. An example could be someone hurting themselves on company property, the details need to be logged in the incident log report book. Another example could be the phone system going down in a call centre, this needs to be managed and alternative arrange plans in place like re-routing to alternative call centre to prevent organisation looking business.
Remote Access Policy defines acceptable methods of remotely connecting to the internal network. If working from home you will be connecting to internal network and systems.
Disaster Recovery Policy. When something serious goes wrong in an organisation, At this point cybersecurity and IT teams will be involved to create a disaster recovery plan depending on size of incident and who is affected
The maximum fine under the GDPR is up to 4% of annual global turnover or €20 million – whichever is greater – for organisations that infringe its requirements.
However, not all GDPR infringements lead to data protection fines. Supervisory authorities such as the UK’s ICO (Information Commissioner’s Office) can take a range of other actions, including:
Fines of up to €10 million or 2% of annual global turnover can be issued for infringements of articles:
Fines of up to €20 million or 4% of annual global turnover can be issued for infringements of articles:
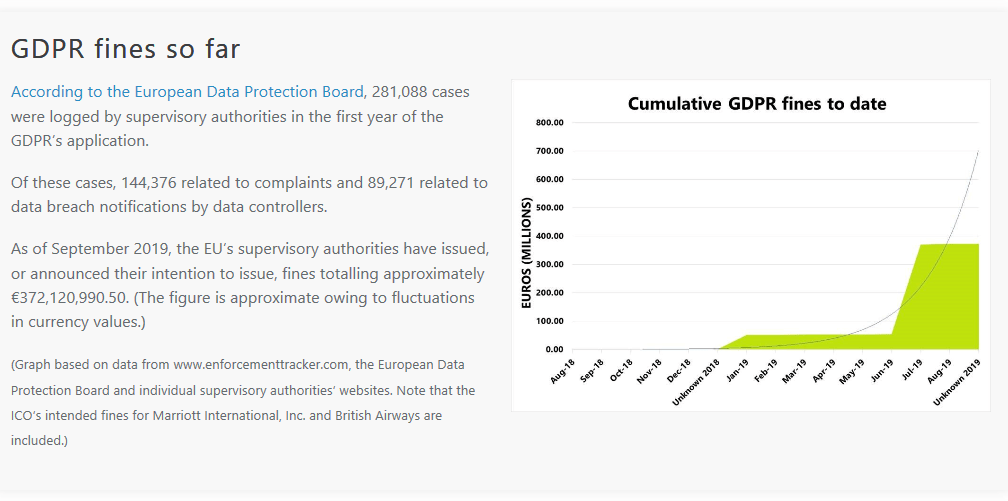
information reference to https://www.itgovernance.co.uk/dpa-and-gdpr-penalties

Below are some differences found online to explain the difference between Data Protection and GDPR
being ‘GDPR’. We thought this table may be of benefit to you.
| DPA(Data Protection Act 1998) | GDPR (General Data Protection Regulation) |
|---|---|
| The Data Protection Act was developed to give protection and lay down rules about how data about people can be used. The 1998 Act covers information or data stored on a computer or an organised paper filing system about living people. | EU General Data Protection Regulation (GDPR) in Europe, adopted in 2016, will be directly applicable starting on May 25, 2018, and will replace the DPA |
| Only applies the UK | Applies to the whole of the EU and, crucially, also to any global company which holds data on EU citizens |
| Enforced by the Information Commissioner’s Office (ICO) | Compliance will be monitored by a Supervisory Authority in the UK with each European country having its own SA |
| Under the current legislation there is no need for any business to have a dedicated DPO | A DPO in some countries will be mandatory for any business or organisation with more than 250 employees |
| There is no requirement for an organisation to remove all data they hold on an individual | An individual will have the ‘Right to erasures – which includes all data including web records with all information being permanently deleted |
| Privacy Impact Assessment (PIA) are not a legal requirement under DPA but has always been ‘championed’ by the ICO | PlAs will be mandatory and must be carried out when there is a high risk to the freedoms of the individual. A PIA helps an organisation to ensure they meet an individual’s expectation of privacy |
| Data collection does not necessarily require an opt-in under the current Data Protection Act | The need for consent underpins GDPR. Individuals must opt-in whenever data is collected and there must be clear privacy notices. Those notices must be concise and transparent and consent must be able to be withdrawn at any time |
| Direction sets aims and requirements, implemented through national legislation | Regulation is binding for all member states |
| Personal data and sensitive personal data | In addition, now includes online identifiers, location data, and genetic data |
| Breach notifications not mandatory for most organisations | Mandatory and within 72 hours |
| Any person who has material damage is entitled to claim compensation | Any person who has suffered material or non-material damage |
| Data protection governance down to best endeavours | Recommendation of a data protection officer to be employed from outside the company for organisations with 250+ employees or more than 5,000 subject profiles per annum |
| Maximum fine is 500,000 | Maximum fine 4% of annual turnover or Euro20M whichever is greater |
| Responsibility rest with the Data Controller | Rests with both the controller and processor with the controller being able to seek damages from the processor |
| Parental consent for minors not required | Parental consent for minors now required |
| Accountability is limited | Accountability fully explicit |
| Subject access requests, £10 per transaction and within 40days | Free of charge and within 30 days |
| Data consent free given, specific and informed | Clear affirmation action with the ability to be withdrawn later |
Digital privacy refers to the protection of an individual’s information that is used or created while using the Internet on a computer, laptop or personal device.
I believe my digital privacy is protected by certain organisations to a certain extent. When we sign up to facebook we are agreeing to the conditions our data is being sold to data miners. Also mistakes are made and we do give our data away quite easily.
Cyber resilience is extremely important because it helps organisations take the necessary measures to address risks, ensuring they can continue delivering their business objectives and outcomes in total confidence, and build trust in business relationships with internal and external customers.
•Cyber resilience is defined as the ability to prevent, detect and correct any impact that incidents have on the information required to do business .
•Cyber resilience differs to cyber security as, in addition to preventing cyber attacks, cyber resilience detects them and corrects the damage.